This service includes 30 days or 7 days of direct implementation work, in collaboration with your organization’s designated intelligence lead. It is not a training program for becoming an analyst or director; those services are offered separately.
Your engagement will be structured during the onboarding call that accompanies this purchase. This call must be scheduled within one week of the transaction date.
Because scheduling reserves dedicated time on our calendar, all bookings become non-refundable once the onboarding call is confirmed.
If your organization requires an offsite intelligence team or ongoing outsourced CTI support, that is a separate service. Please contact indigoint@indigoint.io for assistance in setting up an offsite intelligence engagement.
What You Get in 7 Days
We walk each template, best use cases
We ensure every database if working and connected correctly
We remove template documentation and replace with your actual documentation.
We roll it out to your team and answer questions.
Engagement Model
Onboarding Call: A detailed kickoff session (no time limit) to align stakeholders, clarify goals, define program maturity, and ensure all prerequisites are in place.
Two 4-Hour Working Sessions all week
All materials delivered in a central, organized workspace.
What You Get in 30 Days
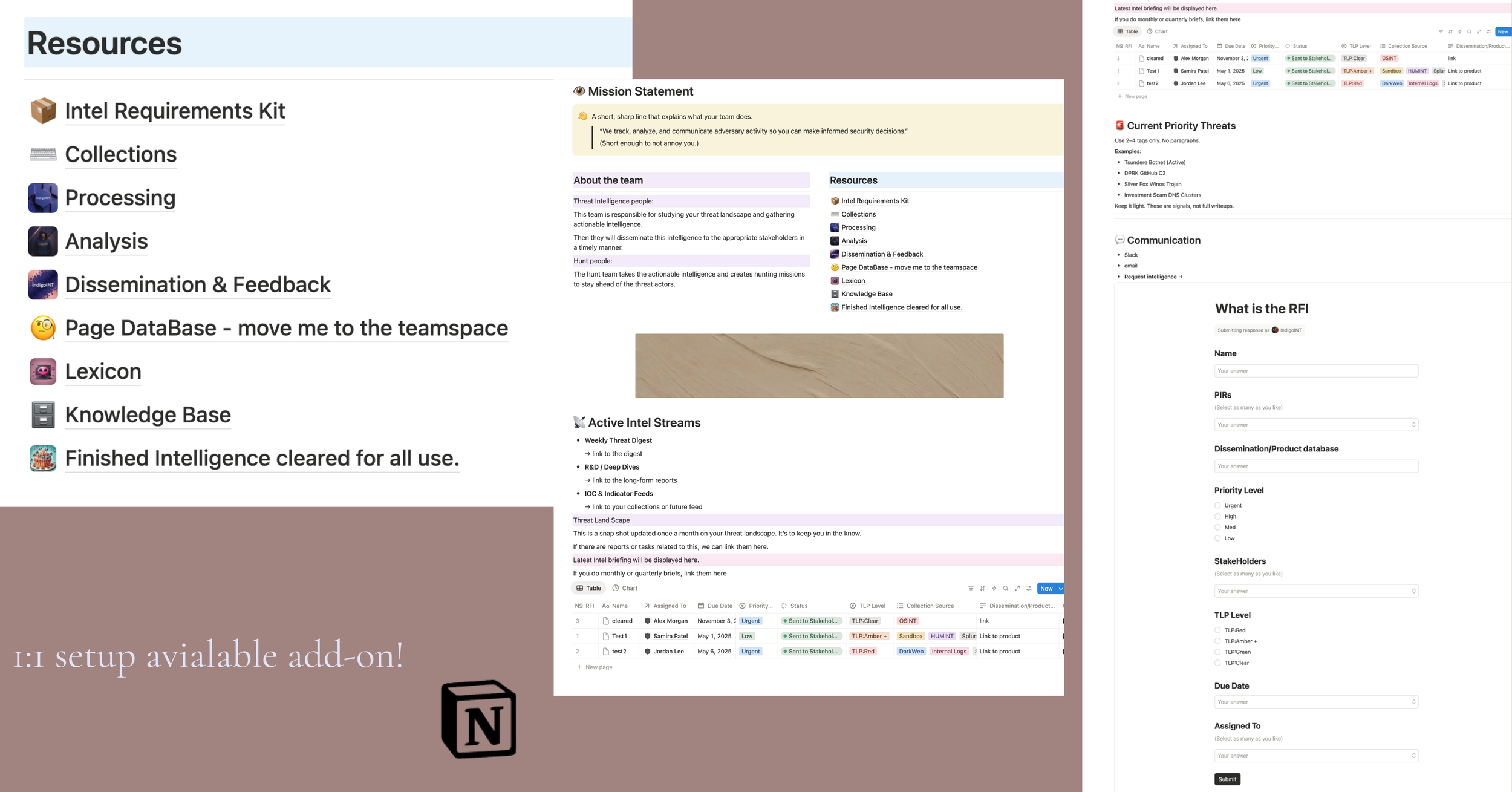
A complete, functional threat intelligence operating system:
Defined intelligence requirements (PIRs/SIRs)
A weekly reporting structure that leadership actually uses
Analyst workflows for collection, analysis, and dissemination
Threat monitoring across relevant sources
Notion-based or internal-system CTI workspace
Repeatable playbooks for long-term use
Week 1 — Stakeholders & Requirements
Week 2 — Workflows & Reporting
Week 3 — Threat Monitoring Setup
Week 4 — Handoff & Training
Engagement Model
Onboarding Call: A detailed kickoff session (no time limit) to align stakeholders, clarify goals, define program maturity, and ensure all prerequisites are in place.
Two 4-Hour Working Sessions:
Mid-Program (End of Week 1): A 4-hour deep build session to solidify workflows, reporting structures, workspace architecture, and stakeholder alignment.
Final Week (End of Week 4): A 4-hour handover, Q&A, refinement workshop, and roadmap delivery to ensure the team can operate independently.
Weekly 30-minute check-ins for direction, clarification, and course correction.
Asynchronous support throughout the engagement.
All materials delivered in a central, organized workspace.